The BCP is the steps required for your organisation to be prepared in the event of an incident.
Required BCP steps
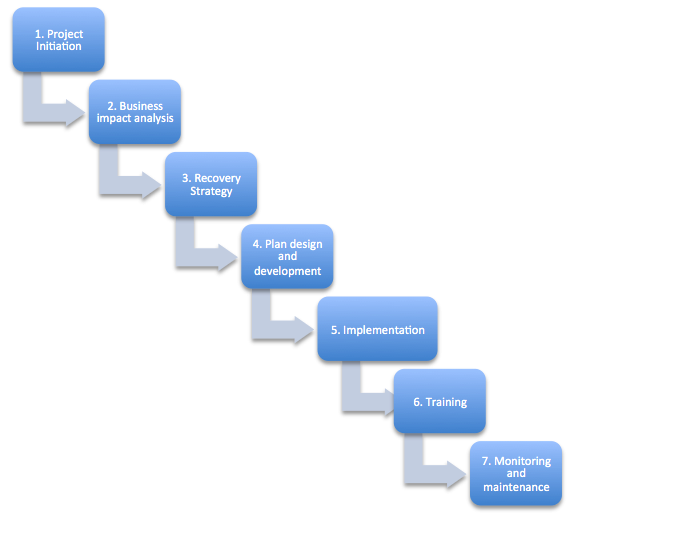
The steps required to build up the BCP within the project
2. Business impact analysis: Value, threats, vulnerabilities
3. Recovery Strategy: Business operations
4. Plan design and development: Response, activation, Recovery, Restoration
5. Implementation: Approval, Training, Documentation
6. Training: Walk-through simulation
7. Monitoring and maintenance: Revise and audit
Project Initiation
1. Analyse the BUs in the organisation
Get the information from the different sources (Accounting, HR, Operations, Commerce, Customer Service)
The team required
BCP Co-ordinator
The spear-head individual who has communication with upper management and the authority to give orders to people
DRP Manager
BCP development team
People from many different departments
Business impact analysis (basically a risk analysis)
There are 4 factors that should be considered
Recovery Strategy
Predefined actions that management has approved in the event of an in incident.
Business process recovery
The workflow diagrams and documents assist the business process recovery by relating it between critical functions
Facility and supply recovery
Hot site - A replica of the primary site and is most expensive. This can also be used for annual testing. (takes about 1hr to be up and running
Warm site - Has the building, electricity though will have 'some' computers 'not all to be up and running (takes about 1/2 days)
Cold site - Least expensive alternative. An empty building with electricity and HVAC. (takes at least 1 week)
Note: Testing must be done at you hot site, or your primary site.
Reciprocal agreement: You can have 2 organisation that share a space in case of a disaster (though hard to enforce)
User Recovery
All about users must recover to achieve normal behaviour
Operations Recovery
The lost of a capability due to equipment failure
To measure the operations recovery...
MTBF = Mean time between Failures
MTTR = Mean time to repair
Best solution would be to have higher MTBF and lower MTTR
Data and Information Recovery
The efforts required to retrieve the data. The solution would be to make backups.Common medias are as follows:
- 8mm tape
- CDR/W media (recommended for temporary storage only)
- Digital Audio Tape (DAT)
- Digital Linear Tape (DLT)
- Quarter Inch Tape (QIC)
- Write Once Read Many (WORM)
Types of backups
Full Backup a complete backup (mainly weekly)
Differential Backup Any changed made during a full backup (daily basis)
Incremental Backup Takes a back up from the last incremental or last full backup. The fastest to backup though takes longer to restore
Continuous Backup constant flow of backups to the database. Example, Hierarchical storage management
Software escrow agreement: A separate location where a company can collect the source code
Plan Design and Development
Implementation
Testing
Disaster life cycles
The teams involved
Recovery team
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

