Risk, as I mentioned, is highly valuable for corporate decision making. It allows the steering committee to review the risk assessments and allows them to make tactical or strategic decisions. When you approach upper management highlighting firewall ACL configuration deficiency require many man-hours, they will initially reject the idea because of the expense and probably the fact that they wouldn't have a freaking clue whatsoever on the issue. Instead, if you stress the severity and the business impact the firewall misconfiguration may cause, then the decision makers could relate and understand the technical issues. The decision makers are ultimately responsible and therefore would have to mitigate the risk meaning they would have to approve the request or accept the problem.
Risk Management
Risk, as I mentioned, is highly valuable for corporate decision making. It allows the steering committee to review the risk assessments and allows them to make tactical or strategic decisions. If a techy-nerd presented to upper management that the "firewall ACL configuration has deficiencies and would require many man-hours", they will initially reject the idea because of the expense and probably the fact that they wouldn't have a freaking clue what the guy is initially on about. Instead, if you stress the severity and the business impact that firewall misconfiguration may cause, then the decision makers could relate and understand the technical issues in hand.
Just a note on that, the decision makers are ultimately responsible and therefore would have to mitigate the risk meaning they would have to approve the request or accept the problem.
Steps to Risk management
1. Identify Assets
- What is tangible (such as asset values) or intangible (such as data trends)
- Not just the cost of assets, A server might be worth $3000 to buy, though because it's a critical server, the repercussions could be catastrophic, not just because of money.
- Qualitative or Quantitative (explained in more detail below)
- Based on cost, would a countermeasure would be even worth implementing?
- (explained in more detail below)
- If there's not definitive decision-making, management have to make a decision
- (explained in more detail below)
1 + 2. Identify Assets + Asset Value
This is fairly intuitive to understand. The scope of objects need to be identified and valued, both tangible and intangible values Delphi Technique (Qualitative Process)
- A manager may influence the employees
- Collecting data anonymously
3. Calculate Risk - Qualitative or Quantitative
You need to decide how to calculate risk, which comes in two ways: Qualitative or Quantitative
Qualitative means it's measured on values, not numbers (most common)
Advantages
- can assign values instead of numbers (High/Medium/low)
- Not as much preliminary work
Disadvantages
- Gut feeling/based on opinion
- Hard to assign money to risk
Quantitative means it's literal values and a tangible measurement (least common)
Advantages
- Able to provide results in monetary values
Disadvantages
- Large amount of data (Loads of preliminary effort)
- Hard to do manually
- Complex Formulas
- No Standards
Qualitative Risk measurements
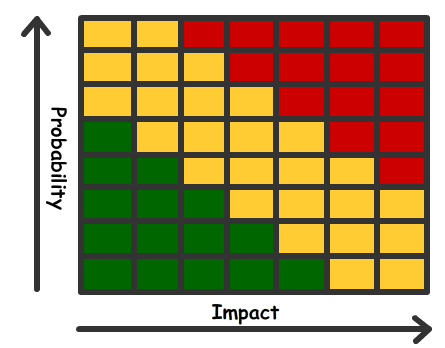
A common qualitative method to determine the severity is constructing a grid based on probability against the impact. Alternatively, you could use the Delphi Technique, which is classed as a qualitative process where they collect opinion-based data from individuals anonymously. This technique ensure that the manager cannot influence the individuals in question.
Quantitative Risk measurements
Quantitative - least common
Quantitative measurements uses monetary values. Were are the common terminologies used
Asset Value
- The actual Value of an object (e.g. Server = $3000)
- The % of damage is an effect happens
- SLE = Asset Value x Exposure Factor
- How often the disaster occurs (used for ALE)
1/year = 1.0
3/year = 3.0
1 every 10 years = 0.1
- Is the expected lost on an annual rate. This includes the single expense and the occurrence
ALE = SLE x ARO
Quantitative Example
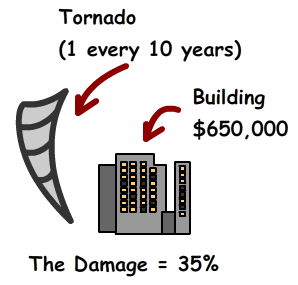
Imagine a tornado is expected to hit the $650,000 office department (1 every 10 years) and it will cause 35% damage.
Single Loss = $650,000 x .035 = $227,500
Annual Loss = $227,500 x 0.1 = $22,750
So the Annual Loss for a tornado will be $22,750. This information can be used in the next stage, cost/Benefit Analysis
Acceptable risk level
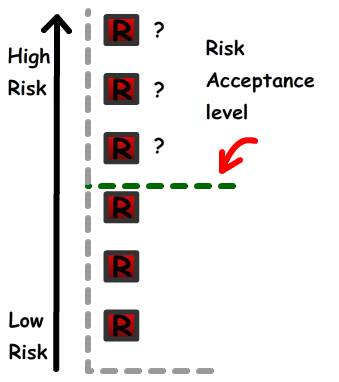
After the assets have been identified, values and measured, it then passed over to management for them to acknowledge and understand the risks.
The analysis will highlight the very-low risks and very-low chance of occurrences so management would happy to accept that risk. They will however require to understand, based on budget and security concerns, the acceptable risk level. This line represents all the risk that can be accepted or requires action. They will need to put countermeasures to mitigate the risk (and bring it below the line) or to eliminate the risk (see uncertainty analysis)
4. Cost/Benefits Analysis
Management needs to determine if the expense of a countermeasure is worth it.
By using the example above, the annual loss of a hurricane is $22,750. For it to be financially beneficial, the cost of the countermeasure needs to be lower than the money lost, otherwise it wouldn't be worth it.
Before Countermeasure expenses = $22,750
Countermeasure implemented = $10,000 (+$30,000 maintenance) = $40,000 Total
In this situation, the countermeasure is more expensive than a solutions, so it's not worth it. If it's not resolved, it then needs to be reviewed within the uncertainty analysis.
5. Uncertainty Analysis
If cost/benefit analysis cannot determine if a countermeasure should be introduced, it's then rolled into the uncertainty analysis. This is where management needs to decide what option to take, and they have 4 options
- Risk Acceptance (Add a control in plan)
- Risk Transference Take out insurance with a company like AIG
- Risk Mitigation Do nothing!
- Risk Avoidance Discontinue the process
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

