Access Control is all about the security features that control how users and systems communicate with each other systems and resources. The objective is to protect the systems and resources from unauthorized access.
Introduction
Access Control is all about the security features that control how users and systems communicate with each other systems and resources. The objective is to protect the systems and resources from unauthorized access.
The goal
The objective is to protect the systems and resources from unauthorized access.
Definitions
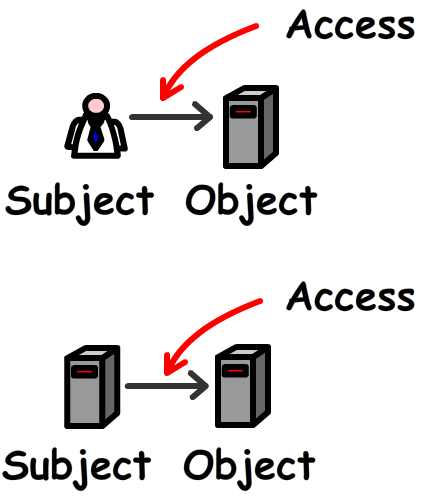
To understanding the concept of access control, we need to understand the relationship between a subject and an object. In every scenario, the subject would always communicate to the Object. For instance, a person may access a file though you may have a computer communicate with another computer (e.g. a firewall through to a web service)
What I'm getting at is that the subject will always communicate to an object
- Access = The flow of information between a subject and an object
Subject = The active entity that requests access to an object
Object = The passive entity that contains information
- Identification = The way of a user claiming an identity to a system (ID card would be a good example) Authentication
= It establishes the user's identity and ensure the user is who they say they are (If you have a credit card, you can authenticate it's yours by entering in the pin number) Authorization
= The specific rights granted to an individual Accountability
= The ability to determine the actions and behavior of a single identity within the system, commonly by audit trails and logs
Authentication can come in 3 ways
- Level 1: Something you know
Level 2: Something you have
Level 3: Something you are
Level 1: Something you know
Something a person knows can be one of the following:
- Password
- PINs
- Lock combination
- Token
- Cards
- Memory
- Certificates
- Synconynous Tokens - Based on a clock/counter
Asynconous Tokens = (Challenge response) based on a time
- Touch-less smart card (uses an antena)
Contact smart card (the card touches the sensor)
Smart Card = Holds data + has a processing power (uses a pin to unlock the info)
- Holds data though does not has any processing power
Level 2: Something you have
Anything something a person have
- RSA Token
- Badge
- Key
Level 3: Something you are
This is all about the physical attributes (biometrics) of an individual.
- False Rejection Rate = Type 1 False Acceptance Rate = Type 2 CER (Crossover Error Rate)
- Note: The lower the CER number the better
Note: Zepher Chart is the better option
Two-Factor (Strong) Authentication
Two factor authentication (a.k.a. Strong authentication) is when you use any 2 of the 3 levels of authentication
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

